TrustiPhi Security Assessment & Recommendation pilot projects give each client a practical, achievable roadmap for full Security Enablement of their products, a stronger security architecture, and in many cases, improved business opportunities.
Security Assessment & Recommendation projects are completed in 2 to 3 months. Your customized Security Assessment & Recommendation may include:
• Security architecture review, analysis, assessment, and recommendations
• Cryptographic design review or development
• Threat model analysis
• Security code review and analysis
Results
The outcome of your Security Assessment & Recommendation will be a practical, achievable roadmap
for Security Enablement, a stronger security architecture, and in many cases, improved business opportunities.
TrustiPhi has helped demanding clients from industry and government:
- Identify and measure risk
- Define practical solutions to lower risk
- Enhance revenue and cost-saving.
Our work has included projects with Intel, Microsoft, Microchip, and Micron.
Benefits of a TrustiPhi Assessment and Recommendation Project
TrustiPhi has in-depth expertise in:
- New technologies – such as Micron Authenta – that may offer you advantages and make new business models and revenue profitable
- New types of threats and recently discovered classes of vulnerabilities
- Internet of Things Readiness
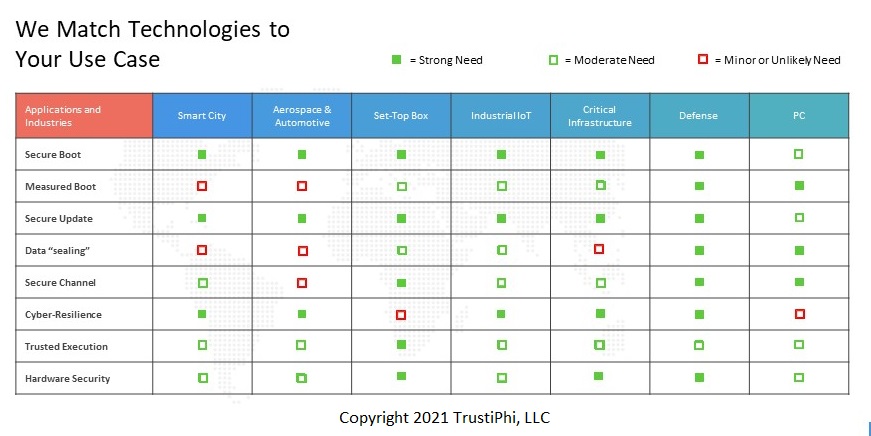
Your hardware security architecture may be strengthened by the independent assessment which TrustiPhi is uniquely qualified to provide. We identify latent security gaps – and opportunities.
Our recommendations enable you to:
- Identify specific assistance that your in-house teams will need
- Demonstrate to your customers that the safety of their data is top priority
- Choose the right turnkey outsourced solution.
- Achieve compliance with regulatory standards, laws, and organizational mandates.
TrustiPhi will deliver the execution plan you need, with steps to achieve security coverage, by incorporating security from the lowest hardware level on up.
Make sure that your product security planning and security architecture are the best practical fit, from technical and business measures. Eliminate “blind alley” exploration of technologies that are not right for your product and business. Equally critical, accelerate and reduce the cost of subsequent development and implementation.
Get Started
We invite you to contact us and set up an initial meeting.

